Extending Einstein's spooky action for use in quantum networks
In Summary
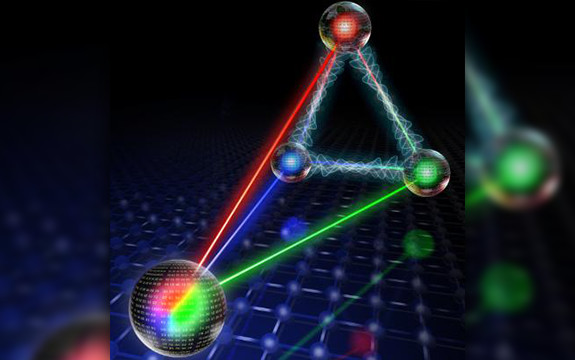
An international team, including researchers from Swinburne University of Technology, has demonstrated that the 1935 Einstein-Podolsky-Rosen (EPR) quantum mechanics paradox may be extended to more than two optical systems, paving the way for exploration of larger quantum networks.
Quantum mechanics is the theory used to describe Nature’s smallest systems, like atoms or photons.
The EPR paradox pointed out that two well-separated systems can have a strange type of quantum connection, so that what happens in one system seems to immediately affect the other.
This connection has recently been called ‘EPR steering entanglement’.
EPR steering is the nonlocality – what Albert Einstein called ‘spooky actions at a distance’ – associated with the EPR paradox and has traditionally been investigated between only two parties.
An experiment performed by researchers from the Australian National University (ANU) and Tianjin University supports the predictions of theoretical work developed by researchers at Swinburne and Peking University.
“We used an optical network to experimentally confirm how this spooky type of entanglement can be shared over not just two, but three or more distinct optical systems,” Dr Seiji Armstrong, from the Quantum Computing Centre Node at ANU, said.
Previously, this sort of entanglement had been studied for only two systems.
“The strength of the entanglement created in our network allows us to confirm rigorously – without using any additional assumptions that would create scientific loopholes – the genuine tripartite entanglement of three of the optical fields. The experiment therefore provides an important step towards validation of mesoscopic quantum mechanics,” Swinburne’s Professor Margaret Reid said.
ANU’s Professor Ping Koy Lam said the experiment also identified properties that may be useful in establishing secure quantum communication networks where shared sequences of numbers created between two parties need to be kept secret from a third party.
The important new feature is that the correlation is established with minimal assumptions about the nature of the equipment used to measure all but one of the fields.
Dr Qiongyi He from Peking University said that this helps in devising strategies, called device-independent cryptography, to outsmart hackers that have may have compromised equipment, such as computers or iPhones.

